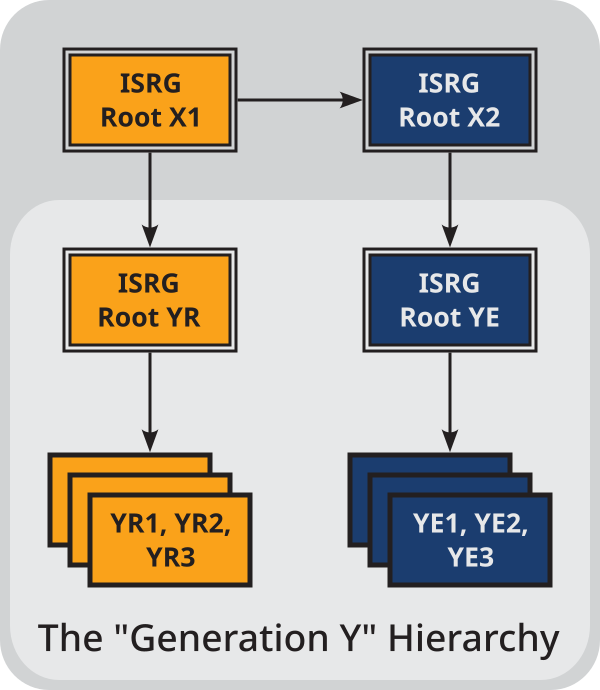
Recently, Let’s Encrypt officially announced its all-new Gen Y Root Certificate Hierarchy (Generation Y Hierarchy). This update introduces two new root certificates (ISRG Root YR and ISRG Root YE) as well as a series of new intermediate certificates.
Without a deeper look, this might seem like just a routine key rotation. But in reality, this architectural adjustment profoundly reflects the dramatic changes occurring in the Web PKI (Public Key Infrastructure) industry. By analyzing this update, we can summarize five core trends for the future of HTTPS and certificate management.
1. Dedicated Roots and Shrinking Trust: The End of Public TLS Client Auth
Trend: The era of “one root certificate for everything” is over. Public CAs will no longer be involved in private identity authentication.
Interpretation: This is the biggest industry rule change behind this update. According to the Google Chrome Root Program and Mozilla Root Store Policy (7.5 Dedicated Root Certificates), future root certificates must strictly follow the “Single Purpose” principle. That is: roots used for website encryption (Server Auth) and roots used for client identity authentication (Client Auth) or email signing (S/MIME) must be completely isolated in the physical trust chain.
Direct impact on developers:
Affected by this standard, Let’s Encrypt has explicitly removed the TLS Web Client Authentication Extended Key Usage (EKU) from intermediate certificates in the Gen Y architecture. This means:
- Current Status: Let’s Encrypt will completely stop issuing certificates with the
clientAuthproperty in 2026. - Future: Solutions relying on public CAs to issue free certificates for mTLS (mutual authentication) between microservices will officially become invalid.
- Action Suggestion: mTLS is essentially a private trust relationship within an organization and should not rely on global public trust. If your business relies on mTLS, please migrate immediately to Private PKI, such as using a self-hosted CA or a Private CA service.
2. Four-Level Certificate Chains Become “Standard Configuration”
Trend: The hierarchy of certificate chains is deepening. The classic “Root -> Intermediate -> Leaf” three-level structure is transitioning to a “Old Root -> New Root -> Intermediate -> Leaf” four-level structure.
Interpretation: In the early stages of the Gen Y architecture, the new root certificates (ISRG Root YR/YE) will be cross-signed by existing old root certificates (ISRG Root X1/X2) to ensure compatibility with older devices globally.
This means that the certificate chain seen by clients is often 4 layers deep. With the shortening of root certificate rotation cycles (for security) and the retention of compatibility requirements (for coverage), this “four-level chain” will become the norm when configuring servers for a long time to come. Developers must ensure that the server side (such as Nginx/Apache) is configured with the complete Fullchain file, otherwise handshake failures and untrusted certificate issues are very likely to occur.
3. Intermediate Certificate “Randomization”: Intermediate Pinning Must Die
Trend: Intermediate certificates will no longer be fixed, but dynamically changing. Any form of intermediate certificate pinning will directly lead to service interruption.
Interpretation: Let’s Encrypt introduced multiple serial number intermediate certificates like YR1, YR2, YR3… in the Gen Y architecture, and will randomly select one for signing during issuance. This means the certificate you issue today might be signed by YR1, and the next renewal might be signed by YR3. If your App or IoT device has hardcoded the fingerprint of a certain intermediate certificate (a common mistake in the past), this upgrade will directly cause connection failures.
Industry Best Practices:
- Preferred Solution: Completely abandon certificate pinning and switch to Certificate Transparency (CT) monitoring logs to ensure security.
- Fallback Solution (If pinning is mandatory): Absolutely do not pin “Leaf Certificates” or “Intermediate Certificates”. You can only pin Root CA (such as
ISRG Root X1and the futureISRG Root YR/YE). - Critical Requirement: Regardless of what you pin, you must configure a “Backup Pin”. That is, include the fingerprint of new root certificates or backup keys that may be enabled in the future in the configuration, otherwise your application will instantly “brick” when the root certificate rotates.
4. The 47-Day Countdown is Set: Certificate Automation is the Only Way to Survive
Trend: The industry is no longer just “discussing” shortening validity periods; a clear timeline has been released. With the passing of CA/B Forum Ballot SC-081, Web PKI will officially enter the era of 47-day validity, and Automated Certificate Lifecycle Management (CLM) will change from a “best practice” to a “mandatory requirement”.
Interpretation: The once undecided “90-day proposal” has now settled and been replaced by a more aggressive roadmap. According to the latest industry standards (Ballot SC-081), the validity period of public trust TLS certificates will be forcibly reduced according to the following schedule:
- March 15, 2026: Maximum shortened to 200 days.
- March 15, 2027: Maximum shortened to 100 days.
- March 15, 2029: Final maximum shortened to 47 days.
What does this mean for operations? A 47-day validity period means that to leave a safety buffer, certificates must be renewed once a month.
- Manual is Dead: Under a 47-day cycle, any operations method relying on manual form filling or even manually triggered scripts will lead to catastrophic service interruptions.
- Certificate Automation is Infrastructure: Only automation tools that support the ACME protocol (such as Certbot, Acme.sh, Caddy, etc.) can handle this frequency. Future server configurations should no longer have hardcoded certificate paths, but should fully shift to a dynamic, automatically rotated certificate management architecture.
- Action Suggestion: Immediately stop all manual certificate application processes. Before the first wave of reductions in 2026, ensure that all your edge nodes, load balancers, and internal services have deployed an Automated Certificate Management Environment.
5. Crypto Agility and “Post-Quantum” Preparation
Trend: PKI architecture design is beginning to emphasize “Agility” to prepare for a smooth transition to Post-Quantum Cryptography (PQC).
Interpretation: The naming convention of Gen Y (YR1, YR2…) and the comprehensive support for ECDSA P-384 demonstrate extremely strong scalability.
- Algorithm Agility: Serial number naming means that when PQC algorithms (such as ML-KEM/Kyber) are introduced in the future, it is only necessary to add new intermediate certificate sequences without overturning the existing architecture.
- Higher Strength Standard: The new architecture vigorously promotes the P-384 curve. Compared with the traditional RSA 2048/4096, it maintains extremely fast handshake speeds while providing higher security. This is also the best transitional solution for the industry before PQC standards are fully implemented.
Summary:
Let’s Encrypt’s Gen Y architecture is not just an upgrade, but an “industry manifesto”. It tells us: Future Web security will be built on shorter cycles, stricter isolation, deeper automation, and more agile architectures.