The foundation of trust on the internet is quietly evolving. You may have noticed that the little padlock in your browser’s address bar is becoming more common, indicating that a website uses HTTPS encryption—something that relies on SSL certificates. Today, a significant industry development may have a profound impact on all website operators: the CA/Browser Forum (CABF) has passed a proposal called SC-081, which plans to gradually reduce the maximum validity of publicly trusted SSL certificates to just 47 days! What does this change mean, and how will it affect us? Let’s dive in.
What is an SSL Certificate and Why is it Important?
Before we discuss the shortening of certificate validity, let’s briefly review the importance of SSL certificates. Think of them as a website’s “digital ID card,” serving two main purposes:
- Encrypted Communication: Certificates encrypt data transmitted between your browser and the website server, preventing third parties from intercepting or tampering with information, and protecting user privacy and data security.
- Authentication: Certificates verify the website’s identity, ensuring you’re visiting the real site and not a phishing page.
Websites with SSL certificates use the HTTPS protocol, and the padlock in the address bar has become a key indicator of a site’s trustworthiness.
The History of Shortening Certificate Validity
This isn’t the first time certificate validity periods have been shortened. Looking back, it’s been a continuous process:
- Early days: TLS certificates could be valid for several years.
- 2012: Maximum validity limited to 60 months.
- 2015: Reduced to 39 months.
- 2018: Further reduced to 825 days (about two years).
- 2020: Driven by Apple, the maximum was limited to the current 398 days (about one year).
Now, with the CABF’s SC-081 proposal, the validity period will be drastically shortened again.
A Closer Look at the SC-081 Proposal
SC-081 stands for “Introduce Schedule of Reducing Validity and Data Reuse Periods.” The proposal covers not only certificate validity but also limits on domain validation data reuse.
Key Points:
Certificate maximum validity will be gradually reduced to 47 days:
This will happen in stages:
- From March 15, 2026: Maximum validity is 200 days.
- From March 15, 2028: Maximum validity is 100 days.
- From March 15, 2029: Maximum validity will finally drop to 47 days.
Domain validation data reuse periods will also be shortened:
- Non-SAN validation data reuse: Eventually reduced from 825 days to 398 days.
- SAN validation data reuse: By March 2028, reduced from 398 days to just 10 days.
| Date | Non-SAN Validation Data Reuse | SAN Validation Data Reuse | Max Certificate Validity |
|---|---|---|---|
| Before 2026/03/15 | 825 days | 398 days | 398 days |
| 2026/03/15 ~ 2027/03/15 | 398 days | 200 days | 200 days |
| 2027/03/15 ~ 2029/03/15 | 398 days | 100 days | 100 days |
| After 2029/03/15 | 398 days | 10 days | 47 days |
A quick explanation of Non-SAN and SAN validation data reuse:
- Non-SAN validation data reuse: SSL certificates come in three types: DV, OV, and EV. DV (Domain Validation) certificates require only domain ownership verification; OV (Organization Validation) and EV (Extended Validation) also require business verification, with EV being stricter. “Non-SAN validation data” generally refers to organization information. In the future, OV and EV certificates will require organization revalidation every 398 days.
- SAN validation data reuse: SAN refers to the domains or IPs included in an SSL certificate. Currently, after validating a domain for an OV/EV certificate, that validation is valid for 398 days. Soon, this will be shortened to 10 days—after which domain ownership must be revalidated.
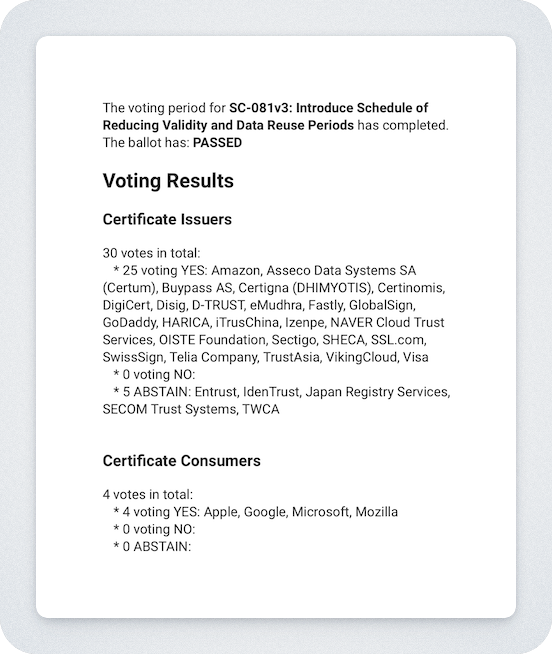
The Proposal Has Passed:
Notably, this proposal has received broad support from CABF members and has been approved. Major browser vendors like Google, Apple, and Microsoft, as well as CAs like Sectigo and DigiCert, voted in favor.
Why Shorten Certificate Validity?
Shortening certificate validity isn’t arbitrary; it’s driven by multiple security and industry trends:
Enhanced Security: The shorter the validity, the less damage a stolen or misissued certificate can cause.
In 2011, hackers breached DigiNotar and misissued hundreds of fake certificates, including for high-value domains like Google. Because these certificates had long validity periods, attackers could use them for man-in-the-middle attacks for some time before they were discovered and revoked. Shorter validity would have greatly reduced the window of exploitation and the number of affected users.
Last year, Entrust misissued over 26,000 EV SSL certificates and failed to revoke them promptly. Longer validity would have increased the risk of abuse. The eventual distrust of this CA by browsers highlights the risks of long-lived certificates.
Improved Reliability: Ensures that domain ownership and organization info in certificates are up-to-date.
SSL certificates often contain information about domain owners and, for OV/EV, organization details. Over long validity periods, domain ownership or organization info may change, making certificates inaccurate and less trustworthy.
For example, if a domain is maliciously acquired but still holds a long-valid OV/EV certificate, attackers could impersonate the previous legitimate organization for phishing or fraud. Shorter validity and more frequent validation reduce this risk.
Better Validation Practices: More frequent validation reduces the risk of misissuance and encourages stricter CA processes.
CAs must verify applicant identity and domain control before issuing certificates. With long validity, only one check is needed for the entire period. Shorter validity means more frequent checks, pushing CAs to improve their validation processes and reduce misissuance. In 2018, the Trustico/Symantec revocation incident exposed risks in the certificate management chain. More frequent updates and validation could help catch such issues earlier.
Promotes Automation: Extremely short validity makes manual certificate management nearly impossible, pushing website owners to adopt automated certificate lifecycle management (CLM) tools like ACME.
With 47-day validity, manually tracking and renewing certificates becomes tedious and error-prone for organizations with many certificates. Automation tools (like ACME) can handle issuance, deployment, and renewal, improving efficiency and reducing outages from expired certificates. Even large organizations like Equifax, Azure, Google Voice, Microsoft Teams, and Apple have suffered outages due to expired certificates. Mature automation could have prevented these incidents.
Security Even Without Revocation: Short validity limits the window for abuse even if a certificate isn’t revoked in time.
Existing revocation mechanisms (CRL, OCSP) aren’t perfect and can be delayed or incomplete. If a stolen or misissued certificate isn’t revoked promptly, it can still be abused during its validity.
Short validity acts as a built-in safety net: even if revocation fails, malicious certificates will soon expire, limiting the window for abuse.
Promotes Cryptographic Agility: Easier to roll out new, more secure algorithms.
Cryptography evolves, with new, more secure algorithms replacing old, vulnerable ones. With long-lived certificates, it takes longer for the industry to adopt new algorithms.
Shorter validity means certificates are replaced more often, providing opportunities to upgrade to stronger algorithms and improving overall Web PKI security.
Impact on Website Owners and Organizations
Reducing certificate validity to 47 days will have a direct impact on website owners and organizations:
Automation is Key: Manual renewal will become extremely difficult or impossible. You’ll need to deploy automation tools for certificate issuance and renewal.
More Frequent Renewals: Certificates will need to be updated more often to keep sites running smoothly.
Potential Cost Increase: While automation boosts efficiency, some solutions or increased certificate operations may add costs.
Timely Renewal is Critical: If a certificate expires, your site will be inaccessible via HTTPS, severely impacting user experience and reputation.
More Frequent Domain Validation: Shorter SAN validation reuse means you’ll need to validate domain control more often for multi-domain certificates.
How to Prepare? Advice for Website Owners
With these changes coming, website owners should prepare proactively. Here are some tips:
Embrace Automation Now: If you’re not already using automated certificate management, start researching and deploying it. The ACME protocol is a widely adopted open standard for automated renewal.
Choose the Right Management Solution: Depending on your site’s scale and architecture, pick a suitable certificate management solution—whether a cloud provider’s integrated service or a third-party CLM platform.
Focus on DNS Validation: DNS validation is a common automated method. Ensure your DNS setup is correct for smooth automation.
Work with Your CA: Choose a CA that offers good automation support and services.
Plan and Test Ahead: Before new validity limits take effect, thoroughly test your automation workflows to ensure everything runs smoothly.
Stay Informed: Keep up with CABF developments and requirements to adjust your processes as needed.
Conclusion & Outlook
Reducing certificate validity to 47 days is a major milestone in web security, reflecting the industry’s ongoing pursuit of security and agility. While it may pose short-term challenges for website operations, in the long run it will help build a safer, more reliable internet. Automation will be key to adapting—sites that fail to automate may face significant operational pressure. Let’s embrace the change and work together for a safer web!